Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Descrição
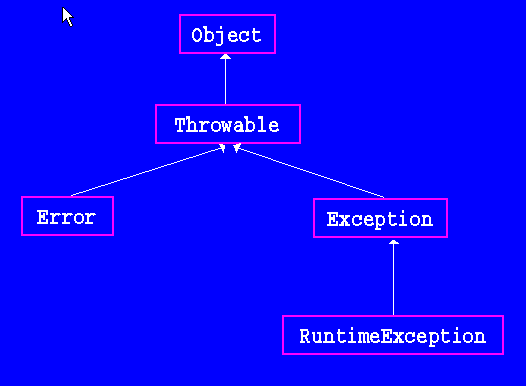
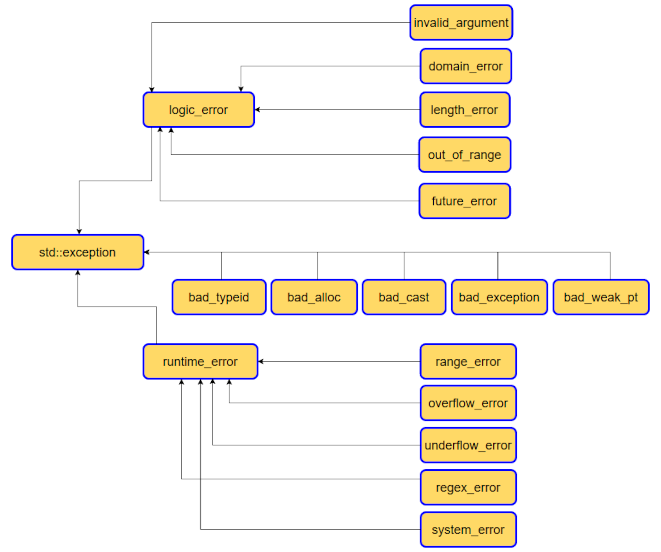
In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.
Aligning Substance Abuse Confidentiality Regulations With HIPAA to
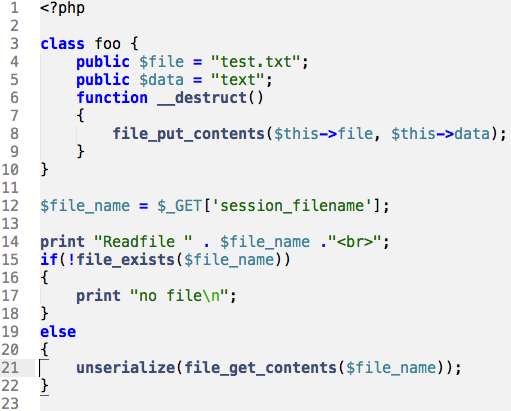
Remote code execution via PHP [Unserialize]
Handle Exceptions - OutSystems 11 Documentation

GitHub Actions Security Best Practices [cheat sheet included]

Hunting for Suspicious Windows Libraries for Execution and Defense

What is a Buffer Overflow Attack Types and Prevention Methods

Top 10 secure C++ coding practices - Incredibuild

Code of Ethics for Government Services Poster
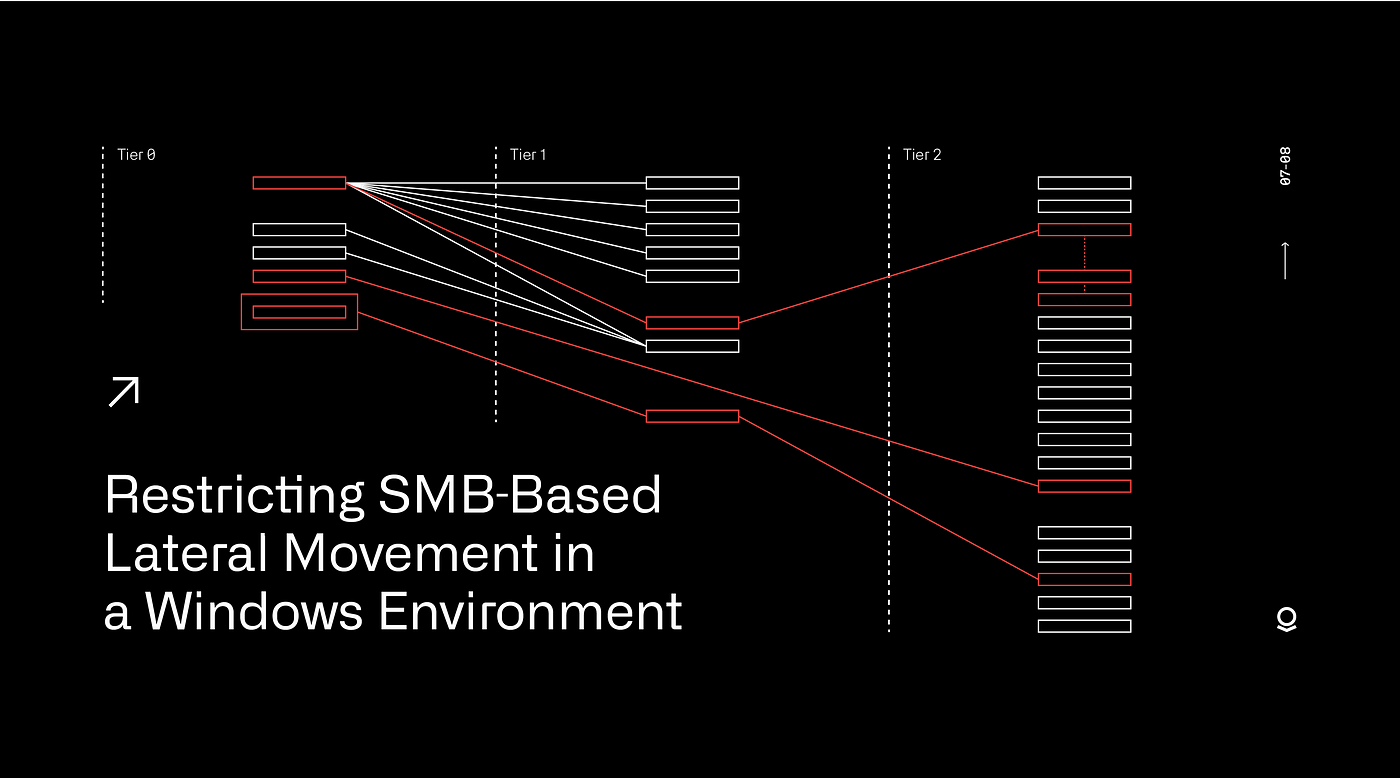
Restricting SMB-based Lateral Movement in a Windows Environment
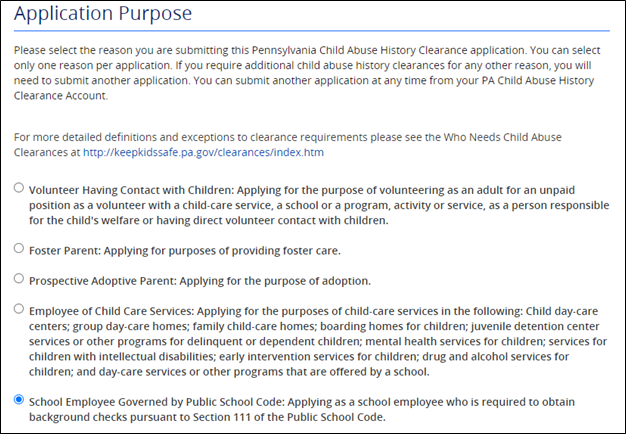
Instructions for Obtaining a Pennsylvania Child Abuse History

RESTful API: How to Manage Rate Limit Abuse
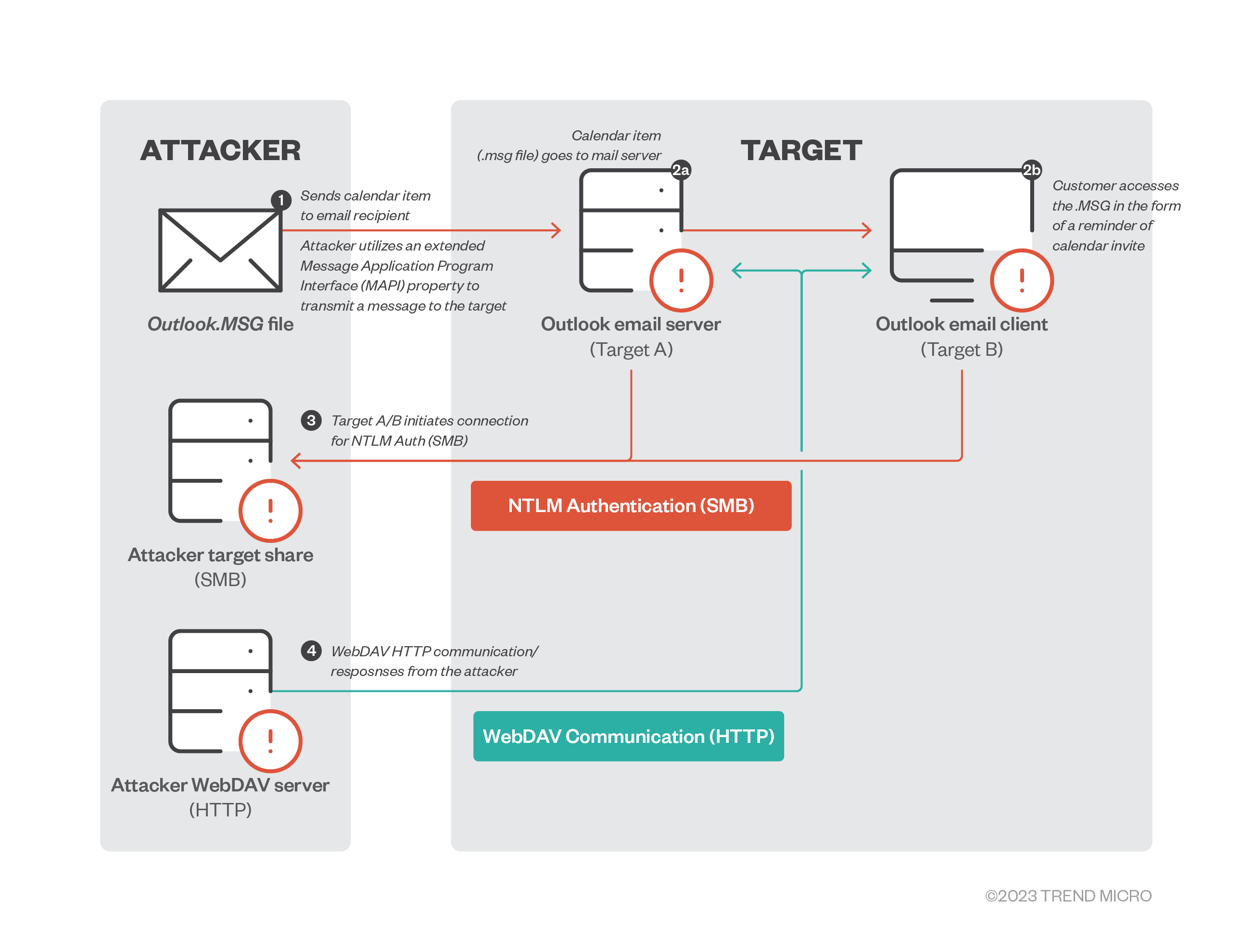
Patch CVE-2023-23397 Immediately: What You Need To Know and Do
de
por adulto (o preço varia de acordo com o tamanho do grupo)