CACTUS ransomware evades antivirus and exploits VPN flaws to hack networks
Por um escritor misterioso
Descrição
CACTUS ransomware operators target large-scale commercial organizations with double extortion to steal sensitive data before encryption.
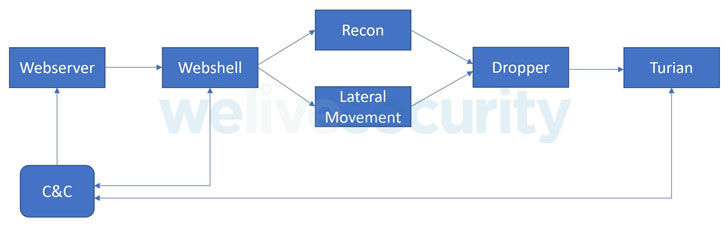
New Cyber Espionage Group Targeting Ministries of Foreign Af - vulnerability database
TuxCare Blog - Insights and News on Linux Technology
Router Hacks and Attacks in the News
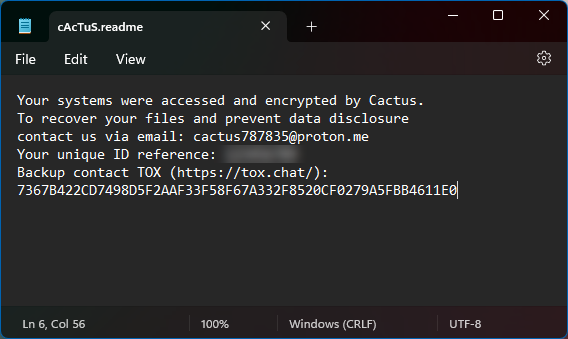
Microsoft Alerts of New Cactus Ransomware Attacks – Gridinsoft
WakeUp Wednesday » Tesorion Cybersecurity Solutions

Lockbit Ransomware: Inside The Cyberthreat And Defense Strategies
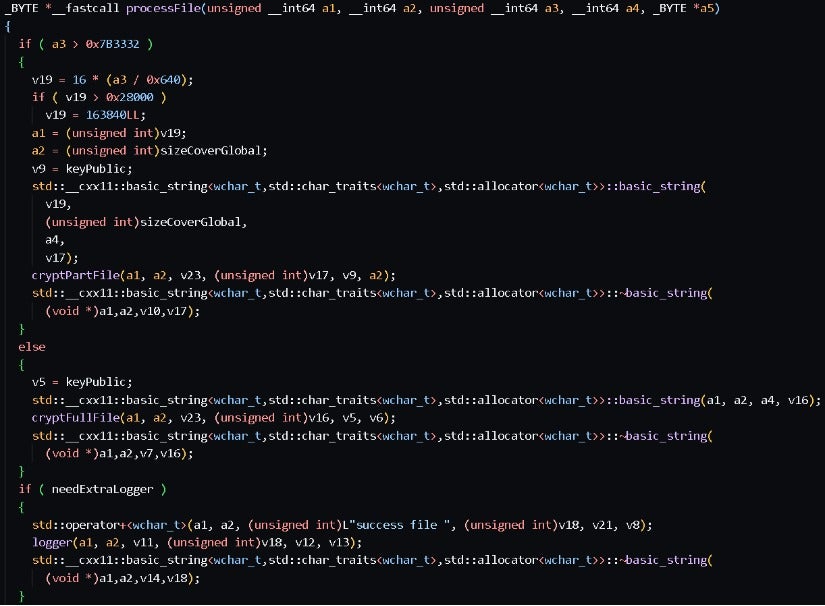
An Analysis of the New Cactus Ransomware

TuxCare Blog - Insights and News on Linux Technology

Hacker Talk • A podcast on Spotify for Podcasters

Mitigating malware and ransomware attacks

Stephen Flynn 💾 (@FlynnInfoSec1) / X
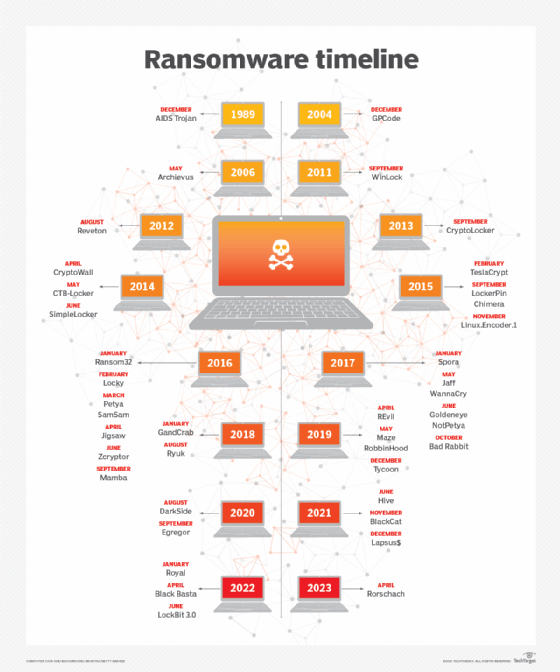
8 Types of Ransomware: Examples of Past and Current Attacks

Cybercriminals Focusing on Microsoft SQL Servers for FreeWorld Ransomware Deployment
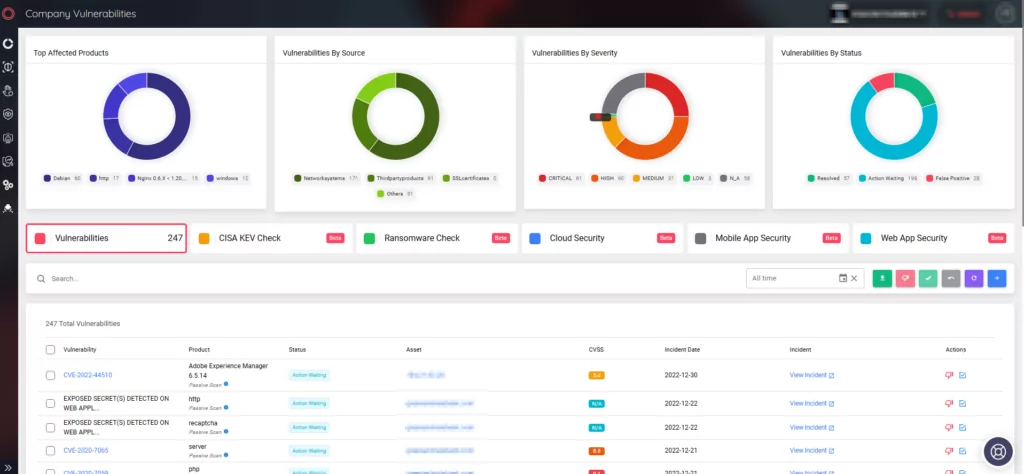
Cactus Ransomware Employs Unique Encryption Techniques to Avoid Detection
de
por adulto (o preço varia de acordo com o tamanho do grupo)